PE Tree, initially developed for internal use is now made available for all security professionals.
Blackberry’s announced at BlackHat USA 2020 that its open-source internal tool PE Tree is now available for all security professionals to use for reverse engineering malware.
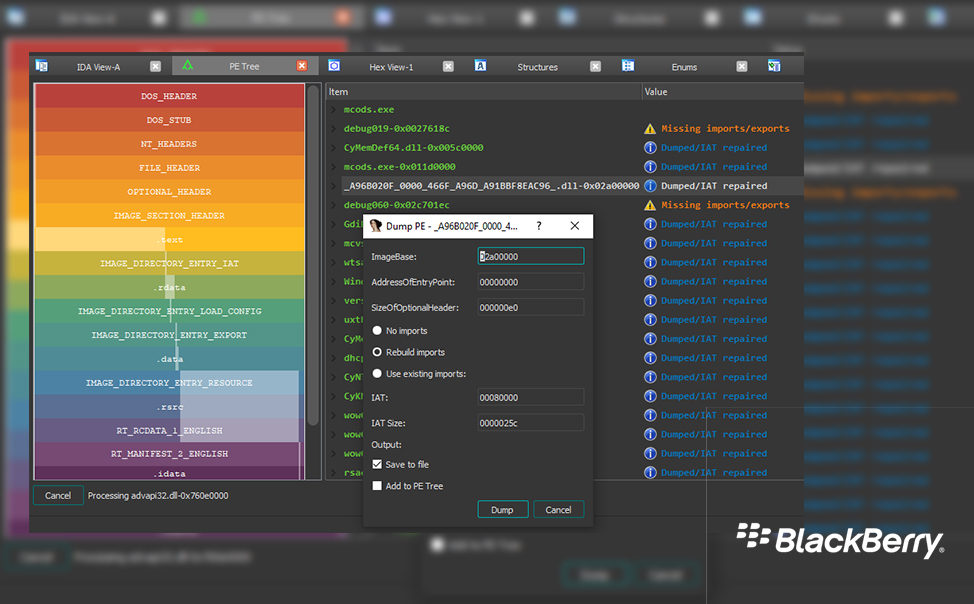
In their press release on August 03 2020 Blackberry stated that, the PE Tree enables reverse engineers to view Portable Executable (PE) files in a tree-view using pefile and PyQt5, thereby lowering the bar for dumping and reconstructing malware from memory while providing an open-source PE viewer code-base that the community can build upon.
The tool also integrates with Hex-Rays’ IDA Pro decompiler to allow for easy navigation of PE structures, as well as dumping in-memory PE files and performing import reconstruction; critical in the fight to identify and stop various strains of malware.
PE Tree was developed in Python and supports the Windows®, Linux®, and Mac® operating systems. It can be installed and run as either a standalone application or an IDAPython plugin, allowing users to examine any executable Windows file and see what its composition is.
“As cybercriminals up their game, the cybersecurity community needs new tools in their arsenal to defend and protect organizations and people,” said Eric Milam, Vice President of Research Operations, BlackBerry.
This free tool for reverse-engineering is under active development and new features will be added frequently.