Google’s monthly Android security patches address 39 problems, including a zero-day vulnerability that is being actively exploited for targeted attacks. According to Google, this vulnerability in the kernel can be exploited for local privilege escalation. This allows a threat actor to access memor...
The Covid19 vaccine scam
Online scammers are adopting new scams that leave no room for doubt. Scams related to Covid-19 have always been active since the start of this pandemic. The previous scam was in connection with the registration of the Covid vaccine. The latest of the online scams surrounding Covid19 is the vaccine...
Attackers using Youtube for their malware campaigns
Threat actors have traditionally exploited embedded links in video descriptions to deliver malware via YouTube videos. According to Frost, a security researcher, there has been a significant increase in malware campaigns on YouTube promoting various password-stealing Trojans. This technique is being...
‘Flubot’ as a threat to Android phones
Flubot malware threatens Android phones again. The first warning about this came from cybersecurity firm Trent Micro. Following this, CERT New Zealand, the government cyber security agency in New Zealand, has come out with a warning. They have tweeted through their official account to be careful not...
ZuRu – A new variety of Mac Trojan horse malware
A new Mac malware known as ZuRu has been discovered spreading in China via poisoned search engine results. Instead of leading to the authentic iTerm2, a free alternative to the default Mac terminal app, the link will redirect you to a malware site that was engineered to look almost identical to the ...
A new insurance model framework for Cyberspace
We have seen a huge increase in cyber attacks in the country since March 2020. The Insurance Regulatory Authority (IRDA) has introduced an insurance model framework in case of leakage or loss of money in a bank account, credit-debit cards, mobile wallets, etc when cyber-attacks and online scams are ...
Cyber Security in the age of COVID19
Since the COVID -19, The situation has been worse all over the world. The global pandemic has led to an increase in cybercrimes in the last one year. The Ministry of Home Affairs’ National Cybercrime Reporting Portal www.cybercrime.gov.in has claimed that over four lakh cyber threat complaints are...
Startups: Why are they targeted?
A decade ago, a company’s technical strategy was not given any importance. Business strategies were considered important. By the end of this decade, the rise of cyber-attacks will be a challenge to be dealt with. India has been focusing on the dream of becoming a leading startup destination in...
Regular cybersecurity checks are vital for any organisation
The earliest news of Cyberattack was heard in the 1970s. and ever since we are witnessing various kinds of updated malware, ransomware, viruses, & so on. With the onset of covid 19 which is forced lot of us to work from home, shop online and many more activities online, take classes online which...
Increasing Cyberattacks on Manufacturing companies
Product manufacturing companies are facing a constant strike of cyberattacks. Morphisec, a US-based software company’s recent research says that 1 out of 5 manufacturing companies has been a victim in the cyberattack. Since the onset of COVID-19, Trojans, info-stealers, and ransomware attacks ...
Digital payment scams on the rise in India
According to a new study performed by YouGov and ACI Worldwide, there is a concern among consumers in India about digital payment scams. The pandemic has been a major catalyst for the adoption and growth of digital payments in India,” said Kaushik Roy, ACI Worldwide’s Vice President. Sin...
Beware of Phishing
A security firm recently detected a 974 percent increase in social-engineering frauds including enticing materials, which are typically focused towards male-sounding names within an agency. For added shock value, the suggestive emails are now being sent to folks at work as follows: Typically, attack...
Ransomware outbreaks to exceed $265 billion globally in the next decade
Ransomware has become one of the most dangerous — and often used — types of malware. When ransomware infects a computer, files are usually encrypted, users are locked out, and payment, generally in cryptocurrency, is required in exchange for a decryption key. The most coommonly scenario related ...
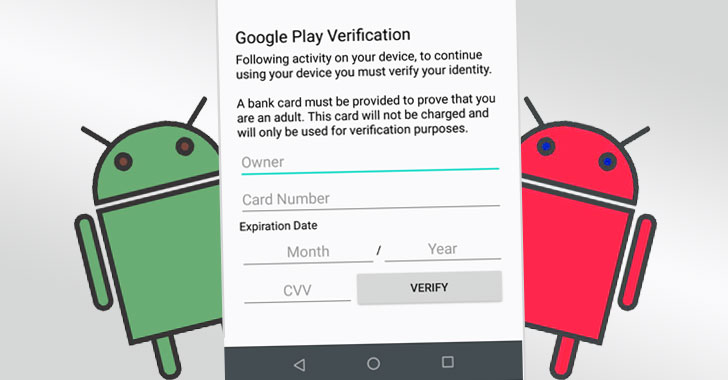
Fake Google Chrome App is stealing bank details
A new android malware in form of a fake Google app is spreading fast. It Targets victims by sending them a message with a link, asking them to pay customs fee to release package delivery. If the unsuspecting user clicks on the link provided, they are asked to update their chrome where they are...
FluBot- New Android Malware
A new android malware called Flubot is a major package delivery scam, targeting Android phones and devices across the UK. It spreads through texts which asks the users to click on the link provided to track their packages. As per NCSC, “The spyware is installed when a victim receives a text messag...
Apple attacked by massive Ransomware Attack
Taiwanese company Quanta, which is one of Apple’s parts suppliers was breached by the group REvil, also known as Sodinokibi. They managed to gain access to new product plans and demanded a ransom of $50 million. The group also released schematics of some of the products to prove that they are not ...
Android malware app spying on WhatsApp users
As per Check Point research team, an android malware app called Flixonline, which was downloadable through the Play store, allowed users to watch global Netflix content free of cost. But in reality, spying on the WhatsApp users. The message that it sent to the users read, “2 Months of Netflix Prem...
Be Cyber secure
Encrypt your data with a password that is difficult to Decrypt. Don’t let anyone violate yours or your clients privacy. Privacy is meant for everyone. Neither Break it nor allow anyone to break it. Invest in cybersecurity service and stay secure against unauthorised access. Find out how secure...
Security is not a Product, but a Process
Coined by Bruce Schneier, he said “Security is a process, not a product. Products provide some protection, but the only way to effectively do business in an insecure world is to put processes in place that recognize the inherent insecurity in the products. The trick is to reduce your risk of expos...
Facebook Hacked
More than 500 million accounts hacked. User data including IDs, full names, locations, birthdates, and email addresses available on hacker’s website. As per Facebook spokesperson, “This is old data that was previously reported in 2019. We found and fixed this issue in August 2019”. Dat...
German Parliament targeted in a Spear Phishing Attack
In a yet another attack after 2015, German parliament has been targeted by hackers. Newsmagazine Der Spiegel reported on Friday that German politicians were sent phishing emails. It is suspected that the attack was carried out by a persistent Russian military intelligence hacking group called Ghos...
VAPT (Vulnerability Assessment and Penetration Testing)
Safe & secure data and communications is of utmost importance for an enterprise to grow business securely. With cyberattacks on the rise, no industry is safe. To protect the data and systems from malicious attacks by ever evolving tools & tactics of cybercriminals, its vital to assess ...
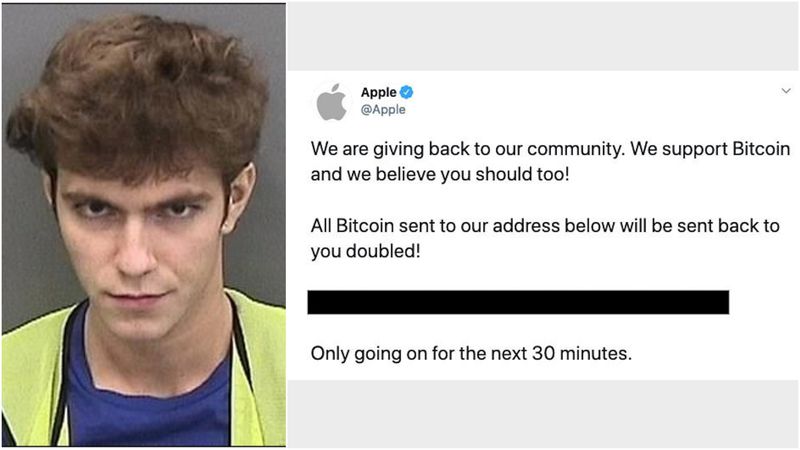
Clark sentenced to three years in prison for Bitcoin Scam of July last year
Clark a teenager is found guilty for bitcoin scam of July 2020. Graham Clark used social engineering to target Twitter employees, has been sentenced to three years in prison. He gained access to various high profile twitter accounts by using different hacking and social engineering techniques and ra...
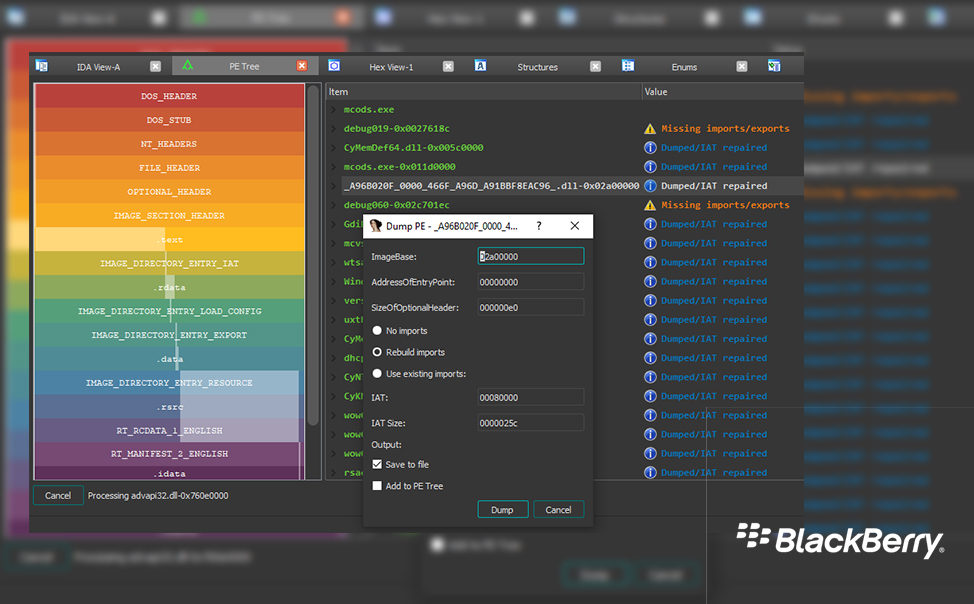
PE Tree – Free Open Source Tool Announced by BlackBerry to Fight Cybersecurity Attacks
PE Tree, initially developed for internal use is now made available for all security professionals. Blackberry’s announced at BlackHat USA 2020 that its open-source internal tool PE Tree is now available for all security professionals to use for reverse engineering malware. In their press...
Phishing attack – Data Breach at University of Utah Health
According to the U.S. Department of Health and Human Services, protected health information (PHI) of patients’ was affected by a data breach at the University of Utah Health. This is the third phishing attack on University of Utah this year. Previous attacks were reported in March and April....
337 Mobile Apps Targeted by New BlackRock Android Banking Malware
BlackRock Android Malware has a wide range of data theft capabilities, the targeted apps include banking, dating, social media, and instant messaging apps. Discovered by security firm ThreatFabric in May this year, this malware is based on the leaked source code of another malware strain Xerxes. It ...
US news sites hacked in WastedLocker ransomware attacks
Researchers with Symantec’s Threat Intelligence team who discovered these attacks confirmed – “dozens of U.S. newspaper websites owned by the same parent company have been compromised by SocGholish injected code”. Using fake software update alerts displayed by the malicious ...
IndiaMART data breached
IndiaMART, India’s largest online B2B marketplace for business products and services with 10 million downloads suffered a breach. Sensitive data of more than 40,000 suppliers is believed to be leaked and sold on online forums. Information leaked include suppliers’ user IDs, full names,...
Office 365 Targeted through Phishing Campaign
Using a sophisticated new phishing campaign, attackers used trusted, recognized brand names to bypass security filters and trick victims into giving up their Microsoft Office 365 credentials to bypass security protections and gain access to corporate networks. Check Point discovered that the campa...
Foodora Data Breach
Foodora, a brand of online food delivery service Delivery Hero has suffered a data breach. Exposing the user account details of 727,000 customers in the following 14 countries: United Arab Emirates, Singapore, Germany, Spain, France, Liechtenstein, Italy, Austria, Hong Kong,...
Microsoft Fixes 129 CVEs in its June 2020 Patch
In its biggest patch Tuesday security update ever, Microsoft released its June 2020 Patch update to fix a total of 129 newly discovered CVEs (Common Vulnerabilities and Exposures). Despite its biggest patch release, none of the vulnerabilities have been exploited in the wild before Microsoft release...
Maze Ransomware Targets VT San Antonio Aerospace
US aerospace services provider VT San Antonio Aerospace was targeted by the Maze Ransomware gang in March 2020. 1.5 TB of unencrypted files and sensitive data was reportedly stolen and now available on public domain in a massive data breach which was discovered on Jun 5. The stolen data incl...
Massive campaign against WordPress websites
In a massive attack on WordPress sites hackers tried to download configuration files by attacking old vulnerabilities in unpatched plugins to steal database credentials. To take over databases, old exploits were used to download or export wp-config.php files from unpatched websites, extract database...
RagnarLocker Group hide their presence by running Virtual Machines
A new technique where ransomware is run from within a virtual machine rather than on a computer is used by the operators of the RagnarLocker ransomware. They are installing VirtualBox- a type of software that lets you run virtual machines to avoid detection and hide from antivirus software. The Ragn...
Retail Organizations Targeted with Phishing and Typosquatting Campaign
Due to COVID-19 pandemic, there has been a steep rise in all kinds of online shopping and services. This rise has given an opportunity to hackers to target retail organisatios with phishing and typosquatting campaign attacks. As the research shows, with the better collection capabilities and an incr...
Thunderspy Attack – Leaves millions of Laptops and PCs Vulnerable
A new flaw called Thunderspy was found by Security researcher Björn Ruytenberg in the security protocols of Intel’s Thunderbolt ports. This can allow the hacker to bypass the login screen and its hard disk encryption to gain full access of Windows or Linux-based computers. The Thunderbolt port ...
Mandrake Android spyware infecting Android devices
Malware known as Mandrake, was detected earlier this year. It has been around since 2016 infecting tens of thousands of users. According to a report by Bitdefender- A newly uncovered strain of Android spyware lurked on the Google Play Store disguised as cryptocurrency wallet Coinbase among other thi...
Security Bugs in WordPress Plugins pose a threat to over million websites
Hackers are exploiting security vulnerabilities in WordPress plugins. This is an active exploitation of the security bugs, which aims to remotely execute arbitrary code. Any registered user can create WordPress websites from scratch and upload arbitrary files, install a backdoor to maintain access, ...
Unacademy hacked! Database of millions of users put up for sale on Dark web
Popular online educational platform Unacademy, with a user base of 14,000 teachers, a million video lessons, and 20 million registered learners is hacked. Database including usernames, emails addresses, passwords, date joined, last login date, first and last names, account profile and account statu...
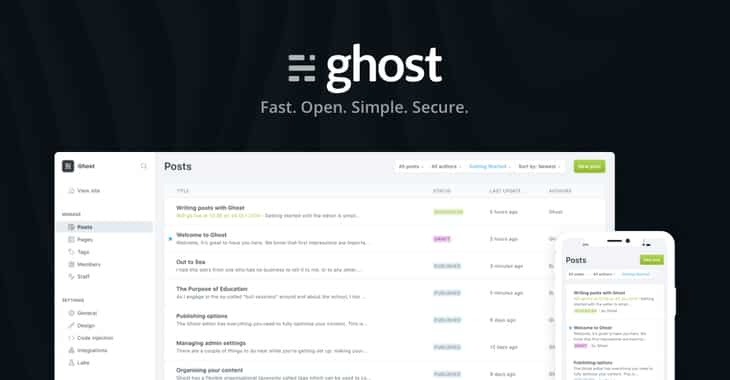
Open-source blogging platform Ghost hacked!
Open source blogging platform Ghost was hacked hours after LineageOS servers got breached with the same vulnerabilities. Hackers exploited vulnerabilities CVE-2020-11651 an authentication bypass and CVE-2020-11652 a directory traversal to take control and to gain remote code execution capabilitie...
Three popular WordPress plugins LearnPress, LearnDash, and LifterLMS hijacked – Critical vulnerabilities found
Amidst Covid-19 pandemic various organizations and universities are using learning management systems (LMS) to manage online courses, host student resources, issue and mark assignments, online registration, assessments, collaborative technologies, payment processing, and facilita...
Viewing a GIF in Microsoft Teams allows hackers to Takeover Accounts
The vulnerability, impacting both desktop and web versions allowed the attacker to access all the data- confidential information, business plans etc. from organization’s Teams accounts by sending a malicious link to an innocent-looking image. Omer Tsarfati from cyberArk’s said, “Even if ...
BEC attack: Florentine Banker steals $1.3 Million from 3 British Private Equity Firms
A sophisticated hacker group named The Florentine Banker managed to trick three British private equity firms and steals $1.3 Million following a complex business email compromise (BEC) attack.As per cybersecurity firm Check Point, nearly $700,000 of the total wire transferred amount is permanentl...
Google Issues critical Warning for Chrome Users
Google has issued a security warning of a critical new vulnerability for Chrome users. They issued a Chrome update that includes a security fix. The new version of the browser 81.0.4044.113 is issued for Windows, Mac and Linux Google only revealed the codename for the exploit CVE-2020-6457 and a vag...
New tool released by Dell: SafeBIOS Events & Indicators of Attack (IoA).
Due to covid-19, many people are forced to work from home, but the network security at home may not be as secure as a corporate network. This is a security risk, that makes terminals vulnerable to malicious actors for stealing data.To enhance terminal security, Dell launched a new security tool call...
Critical update: Webex users phished
An ongoing phishing campaign is targeting remote workers who, due to ongoing covid -19 are relying on conferencing tools like Webex. Hackers are targeting victims with mails claiming to be a Cisco critical security advisory and asking them to update, to steal their Webex credentials. The malicio...
DarkHotel hackers breach Chinese government agencies using VPN zero-day vulnerabilities
DarkHotel hackers, a group believed to be from Korean peninsula, have launched a massive hacking operation at Chinese government agencies and their employees. Attacks believed to be related to the current COVID-19 outbreak, began last month, in March. The invasions were detected by Chinese securit...
Bugs discovered in WordPress plugin, letting hackers gain administrator privileges
A critical vulnerability has been discovered in WordPress Rank Math SEO plugin. With over 200,000 installations, Rank Math helps website owners to attract more traffic to their sites through search engine optimization (SEO). Rank Math is easy to setup, the setup wi...
Hackers exploiting Zoom, Google Hangouts to Spread Malware
Amid covid-19, need to work from home has become a necessity giving rise to popularity of platforms such as Zoom. A per report published by Check Point over 1,700 new “Zoom” domains have been registered since the onset of the pandemic in January, with 25 percent of the domains registe...
Maintain Distance from SpamEmails, Phishing Sites & Alerts
Maintain Distance from SpamEmails, Phishing Sites & Alerts#covid19#covid2020#coronavirus#coronacyberattack#coronacovid More than 2000 Domain Names related to CORONA have been Registered. Beware from Spam Emails, Phishing Sites, Fake Whatsapp Forwards & Cyber Criminals....
China-linked APT HACKERS EXPLOIT CISCO, CITRIX, ZOHO
APT 41, China-linked hackers groups launched a massive cyberattack on countries including Australia, Canada, Denmark, Finland, France, India, Italy, Japan, Malaysia, Mexico, Philippines, Poland, Qatar, Saudi Arabia, Singapore, Sweden, Switzerland, UAE, UK, and USA by exploits that trigger the vuln...
Third-Party App Store Downloads blocked by Google
Google expands its Advanced Protection Program (APP) to all Android users. Earlier the APP was offered to high risk individuals like politicians, business leaders, journalists. It is now available to users with an Android 7.0+ device to improve protection against malicious apps. Signing up for the ...
Cookie Thief – Android Malware stealing browser & Facebook app cookies
Two new Android malware launched to steal cookies from the browsers and Facebook app by gaining the root access on the victim’s Android device. This is an alarming concern as web services use cookies to store on the device a unique session ID that can identify the user without a password an...
Exploiting corona virus fear, hackers target companies
Threat actors are using phishing emails to target and install malware in company systems. Malicious emails mentioning corona virus that appear to be from institutions like CDC are sent in an attempt to get users to open the mail. According to cybersecurity firm Proofpoint Inc., which is monitorin...
T-Mobile Hacked –Employee Emails and Credentials Accessed
Telecom giant T-Mobile’s cybersecurity team discovered a sophisticated cyber-attack on the email accounts of some of its employees. This is a not the first data breach at T-Mobile, revealing personal data of employees and customers. It is not revealed how the attack happened. T- Mobile is in proc...
KrØØk vulnerability affects more than one billion Wi-Fi-enabled devices and access points
The critical security flaw could intercept and allow an attacker to decrypt wireless network packets transmitted by vulnerable devices using WPA2 connections. The Kr00k bug (CVE-2019-15126) affects common Wi-Fi chips Broadcom and Cypress which are built in access points (APs) and smartphones, ta...
Android malware Cerberus can steal Authenticator codes from Google
Cerberus online banking trojan can steal one-time passcodes (OTP) generated through Google Authenticator, by bypassing 2FA (two factor authentication) protected accounts. It’s a new Android banking trojan launched in June 2019 believed to be an elite class of malware with features similar to remo...
ObliqueRAT- A new malware targeting Government organizations
Phishing Email messages are sent to employ ObliqueRat malware targeting government organizations in Southeast Asia. According to experts at Cisco Talos, ObliqueRAT shares similar maldocs and macros with CrimsonRAT campaign from December 2019. The victims receive the threat on endpoint as a malicio...
Haken Clicker Malware affected thousands of Android apps on Google play
New malicious malware in play store apps infects android users. Known as Haken clicker, it takes control over the affected devices to steal user data, subscribe user to premium services and make illegitimate Revenue. There were eight malicious applications in Google Play Store which infected Android...
Iranian origin Malware Campaign Exploiting Vulnerable VPN Servers
Iranian origin malware Fox Kitten Targets Government, IT, Telecommunication, Oil and Gas, Aviation, and Security sectors around the world. This malware attacks networks by exploiting the vulnerabilities in VPN. Hackers secure the remote access to the internal system and networks of numerous companie...
Australian bushfire charity site targeted by cyber criminals
Entire world is familiar with Australian Bush fire, which has burned an estimate of 46 million acres. One billion animals were killed in this tragedy. People around the world are helping Australia to speed up relief process. And then, there are cyber criminals using this tragedy to exploit people wh...
Home and business PC’s exposed by a vulnerability in Dell Support assist
Millions of Dell Computers, both Business & home PCs exposed to vulnerability in Dell SupportAssist software. A preinstalled monitoring tool Dell SupportAssist, on Dell devices has reported a High severity vulnerability. which affects home and business PCs. It allows users to execute arbitrary c...
Bluetooth vulnerability on Android
A newly discovered Bluetooth vulnerability on Android lets attackers execute arbitrary code and silently take remote control of Device without user interaction. Security researchers discovered that Android 8 and 9 were affected by this vulnerability. Android 10 is not vulnerable but it leads to...
Automotive Cybersecurity
Sophisticated Vehicles today are connected with Bluetooth, Wi-Fi and many more apps making our lives easier, safer and more comfortable. Technology is rapidly advancing in the automotive space to meet user’s demand for convenience, also making vehicles susceptible to hackers, opening them to ...
IoT Cyber security
IoT (Internet of Things) is any networking of a device that connects to the Internet in order to exchange data. Electrical devices to home appliances are now connected and can be controlled remotely through internet, they offer convenience in our everyday lives and can also help boost productivity. ...
Restrict Third-party data sharing: FACEBOOK
Most people in the world have at least one Facebook account, making Facebook one of the biggest advertising platforms. Facebook has faced a lot of criticism over privacy and data breach controversies, as it collects users information by tracking their activities on internet. Online apps and websit...
Juice Jacking
A type of physical access attack on a Device or Data, Juice jacking also known as USB scam can be used to install malicious software through public charging stations. At times, using public charging stations is not avoidable, putting us at risk of getting hacked. A USB port can be used as power sock...
Jeff Bezos’ Phone hacked through WhatsApp
WhatsApp, with its end to end encryption security feature trusted by 1.5 billion users around the world, witnessed a high-profile hacking into Jeff Bezos’ phone, allegedly by the equally high-profile Saudi prince Mohammed bin Salman! While we are all vulnerable to...
Social Engineering
A clip from the new Netflix series Jamtara, doing rounds on social media shows how easily a retiree is getting conned out of his life savings through a simple phone call. This type of digital scam is known as social engineering. Social engineering is manipulating human psychology to maliciously gain...
Windows 10 Critical Security Flaw
The existence of a major vulnerability in Windows 10 was confirmed on Jan 14 2020 by the NSA. This is a critical bug that impacts millions of windows 10 users worldwide. Ann Newberg, director cybersecurity NSA, disclosed the vulnerability to Microsoft. Reporting of vulnerability is considered an unp...
2020 Cybersecurity Trends
Make a resolution in this new year to support the cyber defenses of your organization! There are plenty of questions from the cybersecurity point of view on what will be happening in 2020. What are the major trends in technology and what are the risks? Will the attackers want new technologies such a...
Over 267 million Facebook users data exposed online
More than 267 million Facebook users user IDs, phone numbers and names exposed online according to Comparitech and security researcher Bob Diachenko. The information found in the database was fully exposed without any password or other authentication methods, and the researchers believe it was...
10 CyberSecurity:”Resources” You Need to Know
10 CyberSecurity:”Resources” You Need to Know 1. National Institute of Standards and Technology (NIST) NIST, which is the old Department of Weights and Measures, is an agency of the US Government, a sub-department of the Chamber of Commerce. It is non-regulatory and it exists for th...
10 Most Important Cyber Security Tips
1. You Are A Target. Realize that you are an attractive target to hackers. Don’t ever say “It won’t happen to me.” 2. Eight Characters Is Not Enough. Practice good password management. Use a strong mix of characters, and don’t use the same password for multiple sites. Don’t share your pa...
Beware of Stalkerware
Research on commercial surveillance software We told readers that, despite working to protect against stalkerware programs for more than five years, it was time to take our efforts to the next level by spreading awareness of stalkerware and its dangers, and demonstrating how law enforcement, cyberse...
Hacker Steals Over 218 Million Zynga ‘Words with Friends’ Gamers Data
A Pakistani hacker who previously made headlines earlier this year for selling almost a billion user records stolen from nearly 45 popular online services has now claimed to have hacked the popular mobile social game company Zynga Inc. With a current market capitalization of over $5 billion, Zynga i...
New Critical Exim Flaw Exposes Email Servers to Remote Attacks
A critical security vulnerability has been discovered and fixed in the popular open-source Exim email server software, which could allow a remote attacker to simply crash or potentially execute malicious code on targeted servers. Exim maintainers today released an urgent security update—Exim versi...
Hackers abuses Google acquisition domains appspot.com and web.app in latest phishing attacks
These attacks make use of SSL certificates issued by Appspot.com and Web.app. The attackers have designed similar-looking login pages for the domains which are widely used in business. These fake login pages can be used to trick the victims and steal their Usernames and Passwords About domains Appsp...
Research latest: IT managers are struggling to cope with cyberattacks
New research from Sophos suggests that two thirds of organisations were hit by a cyberattack last year. The report lists the three biggest reasons why organisations are still struggling to reduce their risk: Attacks are coming in from multiple directions Cyberattacks are multi-stage, coordinated and...
Attackers stealing credentials using fake Telecom provider’s app
We rely heavily on the telecom industry in this interconnected world, from email and messaging to phone and video calls. This makes the telecommunication industry a favorite target for cyber attackers. The latest concern is an Android-based phishing campaign aimed at customers of Japanese telecommun...
Cyber Security Awareness month
You have a role to play in securing your cyberspace. By adopting cyber security strategies in your daily lives, you can protect your economy, national security infrastructure, personal finances, identity, and privacy. You’ll be one of the two-thirds of the world’s population with interne...
S.O.V.A – The most feature-rich Android malware
In August 2021, Researchers of Threat fabric revealed Android malware SOVA. On Saturday, the new version of this malware grabbed headlines again. Shopping apps, cryptocurrencies, and banking applications are the prime targets. The present-day version also consists of features to steal credentials an...
IoT Device Vulnerability of Baby Monitors
On Friday, Bitdefender researchers revealed the vulnerabilities present in the IoT devices manufactured by a Chinese vendor, Victure. By making use of the zero-day vulnerabilities on a baby monitoring system, attackers can easily get hold of the camera feeds and execute unauthorized code like malwar...